14 Ways To Get Free Amazon Gift Cards
We work hard to bring you insightful personal finance and business content for free. This post includes affiliate partners we think you’ll like. This earns us a commission and helps bring you more great content.
There’s a pretty good chance that you’re an Amazon addict. Don’t be ashamed – plenty of us are.
Nobody can deny that Amazon is one of the best online shopping experiences around. The selection is unimaginably large, the prices are often unbeatable, and the shipping deals make it so that you can have pretty much whatever you want delivered to your doorstep within a couple of days.
That’s why Amazon gift cards are so valuable: they can buy such a wide variety of things that they’re one of the most useful gift cards on the market.
Are you ready to learn a worldview-shattering secret?
You can earn free Amazon gift cards extremely easily these days. Yes, totally free.
The best kind of Amazon shopping experience is an unpaid one, and you can get your very own free Amazon gift cards today!
Check out some of the methods below to see how you can earn free Amazon credit.
1. Survey Junkie
Survey Junkie
At Survey Junkie, you can get paid just to give your honest opinions – which industry decision makers will use to provide better products and services to influence the future consumer landscape!
All you need to do is sign up and create your own profile, which helps Survey Junkie link you to relevant surveys. After you begin to finish surveys, you will accumulate virtual points that you can turn into e-gift cards (like an Amazon gift card) or PayPal cash.
It’s that simple!
Get paid with Survey Junkie now.
2. Swagbucks ($5 bonus)
Ready to score a $5 Amazon gift card just for simply signing up? Look no further than Swagbucks – the site that pays you to log on and use the internet like you normally would.
Just for browsing the web like you usually do, Swagbucks literally pays you in the form of a PayPal deposit or free gift cards, including an Amazon gift card. This can include watching videos, surfing the web in general, answering surveys and playing games.
It’s such a trusted and popular site that they’ve paid out more than $320 million to their users so far. Swagbucks disperses 7,000 gift cards daily, so there are plenty for the taking!
Get free gift Amazon gift cards from Swagbucks here.
3. Drop
Drop
Earning cash back rewards doesn’t need to be limited to just your credit card’s loyalty program. You can earn even more rewards by signing up for Drop – and they are accumulated in addition to your usual credit card rewards.
The Drop app is easy to use: users create an account, link their credit or debit card, add your favorite stores, then start racking up points. The points you build up can then be transformed into a free Amazon gift card, or gift cards from other leading retailers.
Get The Drop app and check out our full Drop app review here.
4. MyPoints ($10 bonus)
MyPoints
With MyPoints, you can score Amazon gift cards by doing one of multiple easy online activities. Seriously!
MyPoints users earn gift cards from popular retailers by completing surveys, watching videos, playing games, and shopping at popular online retailers like Walmart, eBay and Amazon (where you can score as many as 25 points per dollar you spend).
People have already earned $236 million in free rewards from MyPoints, and you can get in on the action today.
Sign up for MyPoints and earn a free $10 Amazon gift card with your first purchase.
5. Ibotta ($10 bonus)
Ibotta
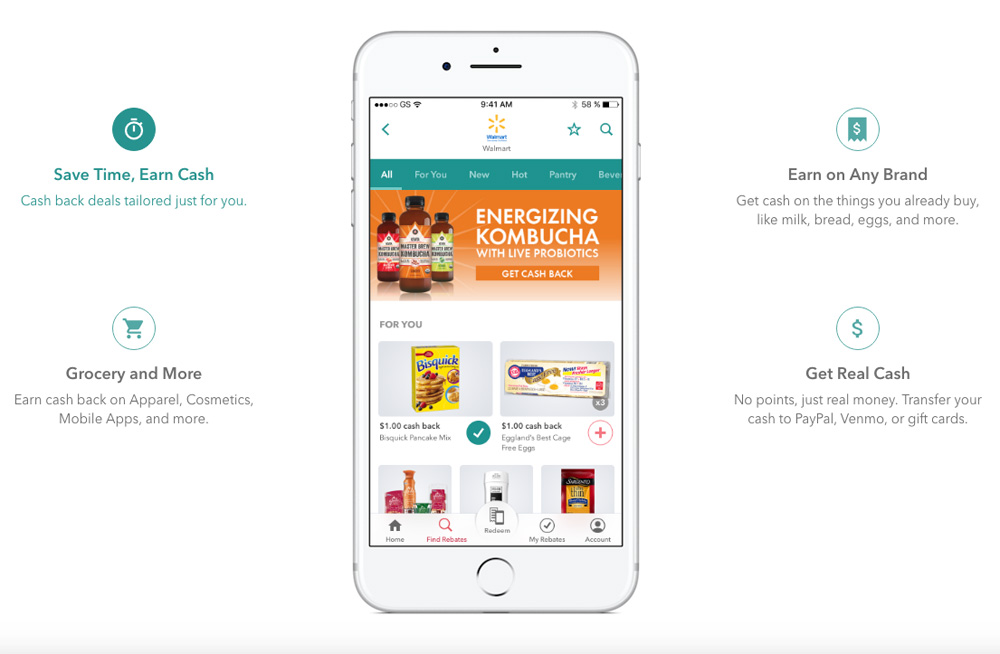
With Ibotta, you get paid just to submit your grocery store receipts, department store receipts, and other types of receipts after you do your normal shopping.
It’s true! Ibotta pays you to simply select items on the app you plan on purchasing, then take pictures of your receipts after you buy them. It’s an easy way to get cash back rewards on clothing, supermarket goods, appliances, and so much more!
How much cash back can you get? Ibotta users can score $1.00 back on body wash, $3.50 back on paper towels, and $20 back on various types of large and small electronics. You can exchange the rewards you accumulate for PayPal credit, a Venmo transfer, or gift cards.
By signing up now, users get an instant $10.00 bonus! You can read about how users of this app score free cash back rewards in our full Ibotta review.
6. Paribus
Paribus
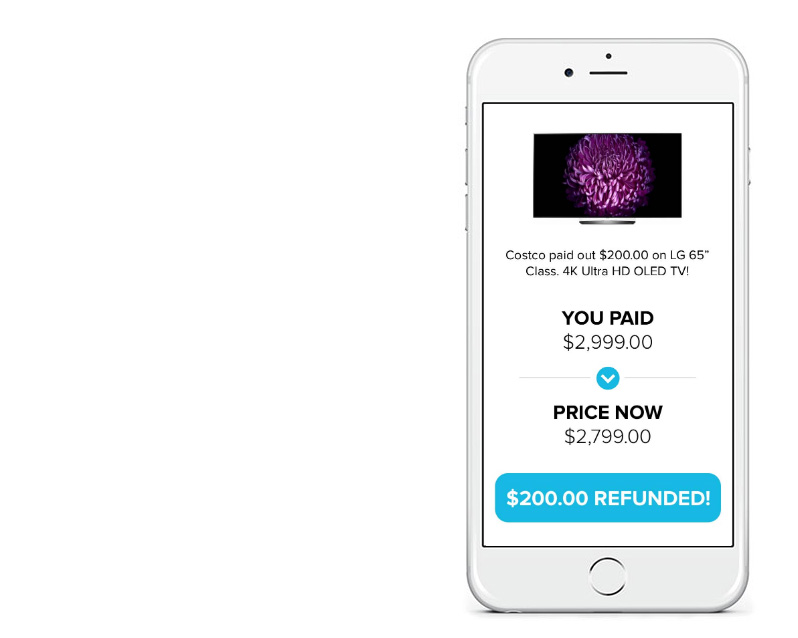
Have you ever checked to see if the price of a recent purchase you’ve made has gone down? Little changes like this often mean we are entitled to a refund – but who has time to keep track?
Many of us are missing out on a lot of savings simply due to the fact that we aren’t getting refunds we’re eligible for. Thankfully, Capital One’s Paribus is here to do all the work for us – and make sure we get the money we’re owed.
Paribus automatically scans the online shopping receipts from your email inbox, and will monitor the prices of your purchase history. Anytime you’re owed money, they let you know!
Aside from cash, you can also earn Amazon gift cards.
Paribus compensates us when you sign up for Paribus using the links provided.
7. Shopkick

Shopkick
Did you know that you can earn Amazon gift cards by just scanning barcodes? It’s true – Shopkick pays you to simply walk into brick-and-mortar retail locations and scan certain items.
As you scan more items, you accumulate points (which they call “kicks”). You can then convert your kicks into gift cards from major retailers. Shopkick enables users to get paid in free Amazon gift cards, too! Start scanning with Shopkick by clicking here.
8. i-Say
i-Say
Want your say to count more? With i-Say, your opinion matters – and actually gets you free Amazon gift cards along the way.
Three million users already earn rewards thanks to i-Say, which rewards people for providing their honest opinion through surveys. After you rack up rewards, you can choose from either Amazon gift cards or pre-paid credit cards. You are in control of which rewards you redeem.
On top of regular rewards, i-Say does regular contests where you’ll get a chance to win even more! Start taking surveys with i-Say.
9. Harris Poll Online
Harris Poll
You may have heard of Harris Poll already, since their market research is frequently quoted in leading news outlets. By becoming a member, you can answer surveys that help influence crucial decisions made by corporations, governments, and non-profit groups.
By providing your unique insights to Harris Poll Online, you get rewarded with rewards from iTunes, Starbucks, and – you guessed it – you can earn Amazon gift cards! Sign up for Harris Poll Online.
10. Inbox Dollars ($5 bonus)

InboxDollars
With Inbox Dollars, you can earn cash back rewards by doing some simple and entertaining online activities, including taking surveys, shopping, playing games and watching videos.
It’s a simple way to earn money, and they have already paid users more than $57 million!
Get an instant $5 credit by signing up for Inbox Dollars.
11. Opinion Square
Opinion Square
Opinion Square not only pays you with cash and other prizes (like free Amazon gift cards), they also give you the unique chance to win their $100,000 sweepstakes when you participate.
Users simply share their thoughts on a variety of topics via email and pop surveys, then start earning cash and prizes. It’s that easy! Sign up for Opinion Square here.
12. Nielsen
Nielsen
You’ve likely already heard about Nielsen research, since it’s a renowned research organization. Well, did you know that they will pay you in free Amazon gift cards if you share your internet usage with them?
It’s true! It’s called the Nielsen Computer and Mobile Panel, and it’s easy to use (and get paid). You simply give them access to your internet-enabled devices, then use the internet like you normally would!
It’s vital data that helps them do market research, and the sign-up process is quick and painless – just register, download the secure app on your devices, and live your digital life like you normally would! Get paid to use your devices like you always do with Nielsen.
13. Mr. Rebates

Mr. Rebates
When it comes to earning cash back rewards, flexibility is one of the biggest draws. With Mr. Rebates, you can redeem your cash back as a PayPal payment, a snail-mailed physical check, or a gift card – including, of course, an Amazon gift card.
All users need to do to earn cash back rewards with Mr. Rebates is sign up via their website, find your favorite online retailers via the Mr. Rebates portal (it’s important to login and start your journey from the Mr. Rebates website), and shop. Your cash back accumulates automatically, and then you can withdraw using your method of choice.
Sign up for Mr. Rebates and earn cash back here.
14. Make the Move to Clean Energy with Arcadia Power

Arcadia Power
You can participate in the green energy revolution and earn free Amazon gift cards at the same time, and it’s simpler than you think.
Think you need to install a wind turbine or a field of solar panels to take advantage of clean energy in your home? Think again!
With a forward-thinking company called Arcadia Power, 250,000 customers have already linked up their home utility service to clean energy projects. You can set up a free account in minutes, and Arcadia Power will connect your own utility ill to local community solar projects and buy renewable energy certificates from wind farms for you.
Arcadia power also actively tracks the market to lower your monthly utility bill – and tells you how much clean energy you helped generate along the way.
Sign up for Arcadia Power and connect your utility bill now to get a free $20 Amazon Gift Card!